The following enhancements and improvements are now available to Censys users.
Platform
- Find the information you need in the Censys Platform faster using the new web app landing page. The new landing page includes a rotating selection of example queries, data aggregations, new onboarding steps, and more.
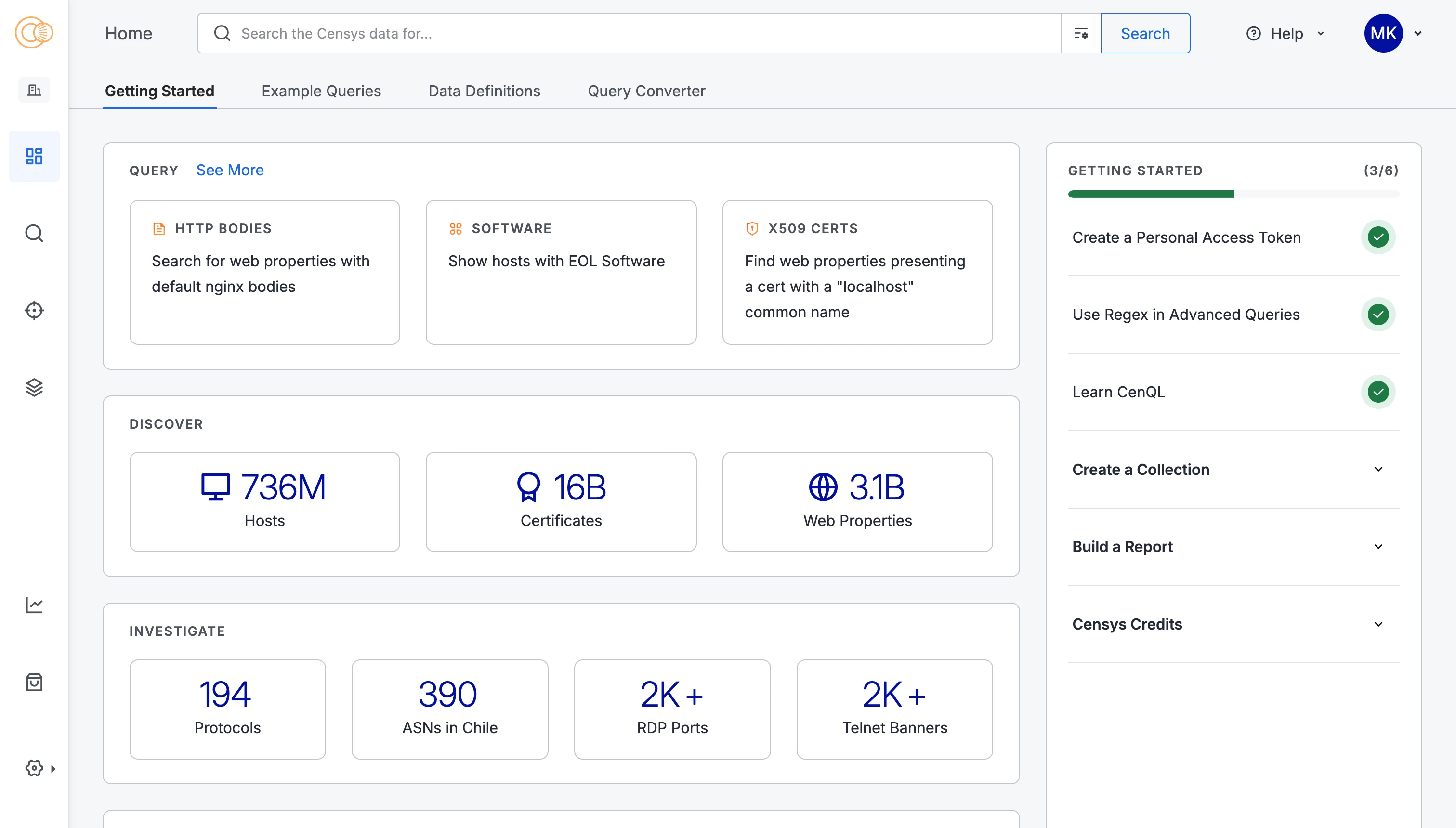
- Use the new Filter my results to display services or endpoints that match my query option on the Report Builder to limit the report results to only the services or endpoints that match your query. This option helps you build more focused reports.
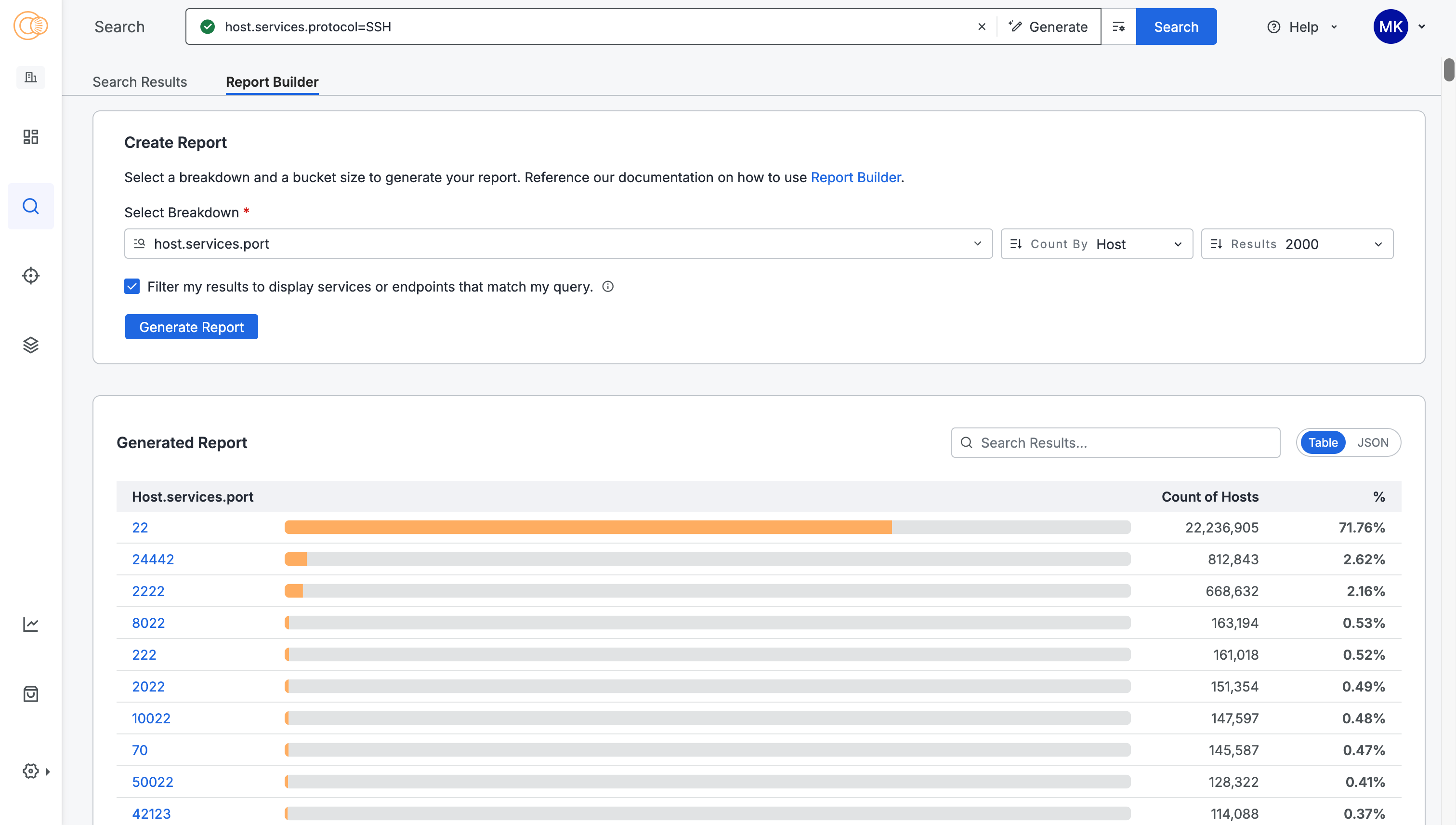
- The maximum number of report buckets has also been increased to 2,000.
- The maximum number of report buckets has also been increased to 2,000.
- Integrate Censys Platform functionality with your automated workflows with the new Python and Go SDKs.
- The Python SDK is also available on PyPI.
ASM
- The new Ports & Protocols Dashboard enables you to understand exactly which ports are open in your attack surface across the full 65,535-port range. This allows you to quickly determine whether there are any open ports that are misconfigured or non-compliant with your organization’s policy.
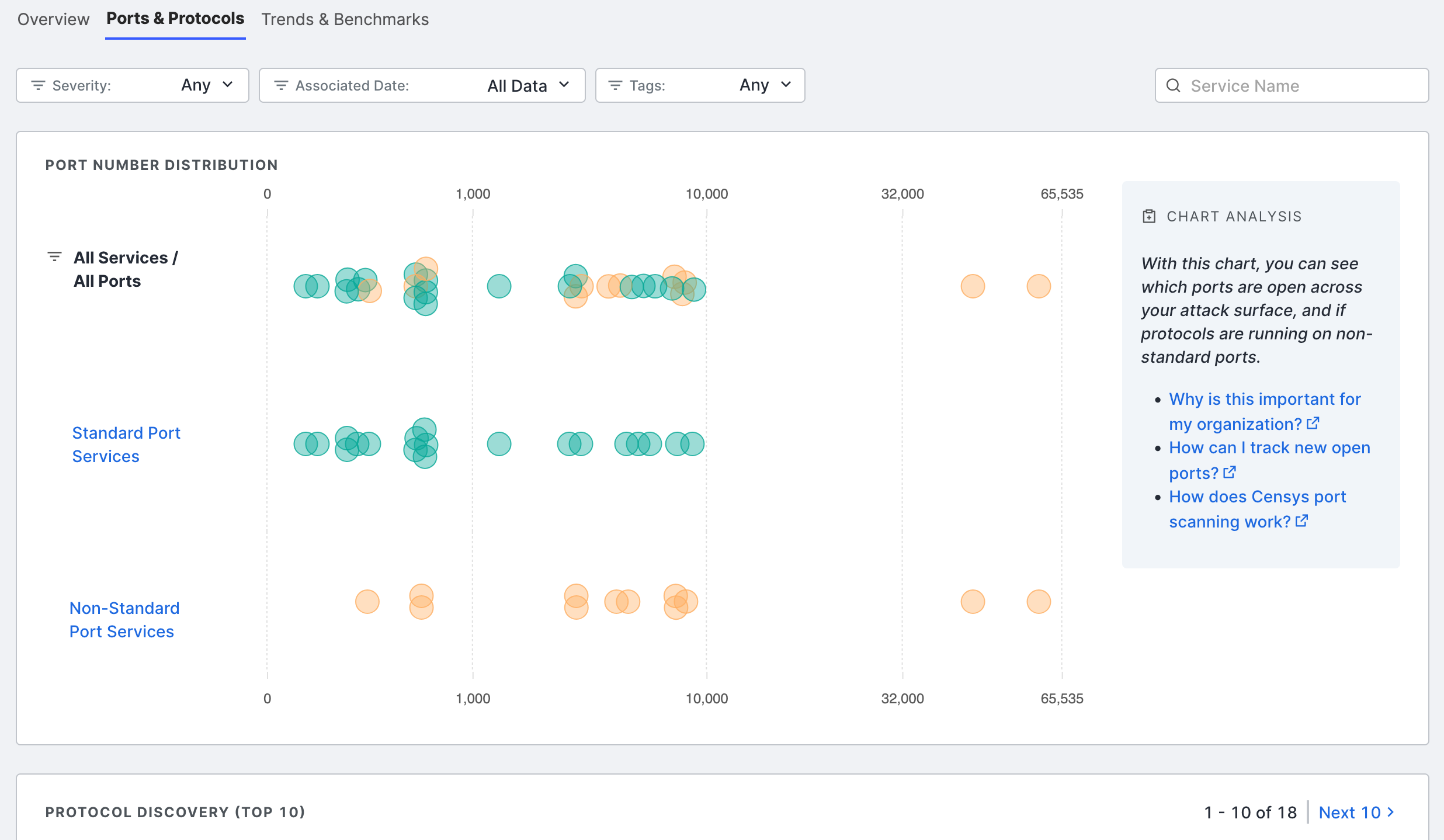
- The dashboard also shows which protocols are present on your ports. ASM identifies whether these protocols are on standard ports, as defined by IANA.
New fingerprints
Added the following fingerprints.
| Type | Name | Description | Query |
| software | DPanel | This is a DPanel Docker Server. | |
| risk | WINRM Service Exposed | Windows Remote Management (WinRM) is a Microsoft protocol used for remotely managing Windows systems via PowerShell and other tools. While powerful for automation and administration, exposing WinRM to the internet is dangerous because it can allow attackers to execute remote commands, especially if using weak or default credentials. It supports basic and NTLM authentication, which can be intercepted or brute-forced, particularly over unencrypted HTTP (port 5985). Without proper safeguards like VPN access,strong auth, and firewalls, an exposed WinRM service is a high-risk entry point for attackers. |

