Product Updates
See all of our release notes and learn about helpful features
- 85 Product updates
- Home
- Product updates
Jan 12, 2026
Censys Release Notes for January 12, 2026
SummaryAdded aliases for Platform threat, screenshot, SHA-1 hash, and organization data fields. Deployed several enhancements to the ASM web UI. One new software fingerprint for Coolify and one new ASM risk fingerprint for n8n services vulnerable to Ni8mare (CVE-2026-21858). Two new Rapid Response advisories: Three Vulnerabilities in Coolify Self-Hosting Platform [CVE-2025-64424, CVE-2025-64420, CVE-2025-64419] n8n Unauthenticated Remote Code Execution (NI8MARE) [CVE-2026-21858] PlatformAdded the following aliases for Platform data fields: threats screenshots sha1 org ASM Several improvements to the ASM web UI were made, including: The workspace selection dropdown is now on the right side of the navigation bar. Icons have been added to many of the items available in the top navigation dropdowns. Scan frequency information is now located at the bottom of the Resources dropdown. Added links to the Integrations dropdown to see all integrations, connected integrations, available integrations, and integrations that need attention. Rapid ResponseThe Censys Rapid Response team published information about and queries for the following issues.Three Vulnerabilities in Coolify Self-Hosting Platform [CVE-2025-64424, CVE-2025-64420, CVE-2025-64419] The following queries can be used to identify exposed Coolify instances. Platform query ASM query Legacy Search query n8n Unauthenticated Remote Code Execution (NI8MARE) [CVE-2026-21858] The following queries can be used to identify exposed and potentially vulnerable n8n instances. Platform query ASM risk query Legacy Search query New fingerprintsAdded the following fingerprints.Type Name Description Query software Coolify This is Coolify, an open-source self-hosted platform for managing servers, applications, and databases. Platform query risk Vulnerable n8n (Ni8mare) [CVE-2026-21858] This is a service running a version of n8n workflow automation platform that is vulnerable to CVE-2026-21858 (Ni8mare), a critical unauthenticated Remote Code Execution vulnerability caused by a Content-Type confusion flaw in the webhook and file handling mechanism. Attackers can exploit this by sending specially crafted HTTP requests to form-based workflows to read arbitrary files, extract credentials, forge administrator sessions, and execute arbitrary commands.. ASM risk query: risks.name: `Vulnerable n8n (Ni8mare) [CVE-2026-21858]`
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Jan 5, 2026
Censys Release Notes for January 5, 2026
SummaryNew software fingerprints for HPE OneView and Hack the Box. New ASM risk fingerprints for SmarterMail services vulnerable to CVE-2025-52691, exposed HPE OneView services, unauthenticated ZeroMQ services, and unauthenticated NATS services. Added support for ingesting and excluding cloud resources from the AWS ap-east-2, ap-southeast-7, and ap-southeast-6 regions when using the ASM AWS Cloud Connector. One new Rapid Response advisory and queries for SmarterMail CVE-2025-52691.ASMASM users can now configure their AWS Cloud Connectors to ingest or exclude cloud resources from the ap-east-2, ap-southeast-7, and ap-southeast-6 regions.Rapid ResponseThe Censys Rapid Response team published information about and queries for the following issue.SmarterMail Unauthenticated Arbitrary File Upload Vulnerability Allows RCE [CVE-2025-52691] The following queries can be used to identify exposed and potentially vulnerable hosts. Platform query ASM risk query Legacy Search query New fingerprintsAdded the following fingerprints.Type Name Description Query software HPE OneView This is an HPE OneView infrastructure management platform. Platform query software Hack the Box This is a Hack the Box service or endpoint. Platform query risk Unauthenticated NATS Service A NATS messaging system is exposed without authentication. This allows unauthenticated clients to publish messages to subjects and subscribe to subjects to receive published messages, potentially exposing sensitive data or allowing unauthorized data manipulation. ASM risk query:risks.name: `Unauthenticated NATS Service` risk Unauthenticated ZeroMQ Service A ZeroMQ service is exposed without authentication. ZeroMQ services allow unauthenticated clients to connect and interact with the messaging system, which introduces a risk of unintended data exposure or manipulation. ASM risk query:risks.name: `Unauthenticated ZeroMQ Service` risk Vulnerable SmarterMail [CVE-2025-52691] This SmarterMail server is running a build version vulnerable to CVE-2025-52691, an arbitrary file upload vulnerability that allows unauthenticated attackers to upload arbitrary files to any location on the mail server, potentially enabling remote code execution. Build versions 9406 and earlier are vulnerable. ASM risk query:risks.name: `Vulnerable SmarterMail [CVE-2025-52691]` risk Exposed HPE OneView An HPE OneView infrastructure management application is exposed to the Internet. ASM risk query:risks.name: `Exposed HPE OneView`
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Dec 29, 2025
Censys Release Notes for December 29, 2025
SummaryOne new Rapid Response advisory, queries, and ASM risk fingerprint for MongoBleed (CVE-2025-14847), a critical MongoDB uninitialized memory disclosure vulnerability.Rapid ResponseThe Censys Rapid Response team published information about and queries for the following issue.MongoBleed - Critical MongoDB Uninitialized Memory Disclosure Vulnerability [CVE-2025-14847] The following queries can be used to identify exposed and potentially vulnerable MongoDB instances. Platform query ASM risk query ASM query Legacy Search query New fingerprintsAdded the following fingerprint.Type Name Description Query risk MongoBleed: Vulnerable MongoDB [CVE-2025-14847] This MongoDB server is running a version vulnerable to CVE-2025-14847 (MongoBleed), an unauthenticated memory leak vulnerability that allows remote attackers to exfiltrate sensitive data from the database server's heap memory without requiring credentials. ASM query: risks.name="MongoBleed: Vulnerable MongoDB [CVE-2025-14847]"
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Dec 22, 2025
Censys Release Notes for December 22, 2025
SummaryNew Platform API endpoints to list active threats and retrieve credit information for Free users. One new Rapid Response advisory for CVE-2025-20393, which affects Cisco Secure Email Gateways. One new software fingerprint for Flowise servers.PlatformUse the get Free user credit details API endpoint to retrieve your Free user account credit balance and refresh information.Threat HuntingUse the list active threats API endpoint to get a list of active threats observed by Censys. Threats are active if their fingerprint has been identified on hosts or web properties by Censys scans. This endpoint is available to organizations that have access to the Threat Hunting module. Rapid ResponseThe Censys Rapid Response team published information about and queries for the following issue.Cisco Secure Email Gateway AsyncOS Zero-Day Exploited in the Wild [CVE-2025-20393] The following queries can be used to identify exposed Cisco Secure Email Gateways. These are not necessarily vulnerable to this CVE. Only appliances with the Spam Quarantine feature enabled are affected. Review any exposed ESA instances in your environment to determine whether Spam Quarantine is enabled; by default, this feature is associated with TCP ports 80, 82, 83, and 6025. Platform query ASM query Legacy Search query New fingerprintsAdded the following fingerprint.Type Name Description Query software Flowise This is a Flowise Server. Platform query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Dec 15, 2025
Censys Release Notes for December 15, 2025
SummaryNew Rapid Response advisory and queries for Ivanti Endpoint Manager Stored XSS Vulnerability [CVE-2025-10573]. New software fingerprints for n8n servers and Apache Tika servers. New ASM risk fingerprints for Fortinet products vulnerable to CVE-2025-59718 and CVE-2025-59719 and Ivanti Endpoint Manager instances vulnerable to CVE-2025-10573.Rapid ResponseThe Censys Rapid Response team published information about and queries for the following issue.Ivanti Endpoint Manager Stored XSS Vulnerability [CVE-2025-10573] The following queries can be used to identify exposed Ivanti EPM instances. Platform query Legacy Search query The following queries can be used to identify exposed and vulnerable Ivanti EPM instances. Platform query (requires Starter license or above to use regex) Legacy Search query ASM risk query New fingerprintsAdded the following fingerprints.Type Name Description Query software n8n Server This is a n8n Server, an open-source workflow automation platform with AI integration. Platform query software Apache Tika This is an Apache Tika Server, a content analysis toolkit. Platform query risk Vulnerable Ivanti Endpoint Manager [CVE-2025-10573] This is a service running a version of Ivanti Endpoint Manager vulnerable to CVE-2025-10573, a critical Stored Cross-Site Scripting (XSS) vulnerability that allows a remote unauthenticated attacker to execute JavaScript in the context of an administrator's browser session, potentially leading to session hijacking and unauthorized administrative actions. ASM query: risks.name: `Vulnerable Ivanti Endpoint Manager [CVE-2025-10573]` risk Vulnerable Fortinet Products [CVE-2025-59718, CVE-2025-59719] This is a Fortinet FortiOS device running a version that is vulnerable to CVE-2025-59718 and CVE-2025-59719, an Improper Verification of Cryptographic Signature vulnerability [CWE-347] that may allow an unauthenticated attacker to bypass the FortiCloud SSO login authentication via a crafted SAML message, if that feature is enabled on the device. ASM query: risks.name: `Vulnerable Fortinet Products [CVE-2025-59718, CVE-2025-59719]`
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Dec 8, 2025
Censys Release Notes for December 8, 2025
SummaryUse aliased fields in the Platform to search across multiple fields at once and quickly find relevant assets. New Rapid Response advisories and queries for: Unauthenticated RCE Flaw in React Server Components [CVE-2025-55182] Critical XXE Injection Bug in Apache Tika [CVE-2025-66516] pgAdmin4 Allows RCE via PLAIN-format Dump File Restore [CVE-2025-12762] New software fingerprints for Waku, pgAdmin4, and Ferron web servers. New ASM risk fingerprints for React2Shell and pgAdmin4 CVE-2025-12762.Platform Some fields are now grouped into aliases to make it easier to search across multiple fields at once. Aliases can be used in the Platform web UI or API. The complete list of aliases and their mapped fields is available in the documentation. Rapid ResponseThe Censys Rapid Response team published information about and queries for the following issues.Unauthenticated RCE Flaw in React Server Components [CVE-2025-55182] The following queries can be used to identify exposed React Server components. Platform query Legacy Search query ASM query ASM risk query Critical XXE Injection Bug in Apache Tika [CVE-2025-66516] The queries below can identify potentially vulnerable Tika instances. Platform query Legacy Search query ASM query pgAdmin4 Allows RCE via PLAIN-format Dump File Restore [CVE-2025-12762] The queries below can help identify potentially vulnerable pgAdmin4 instances. Platform query Legacy Search query ASM risk query New fingerprintsAdded the following fingerprints.Type Name Description Query software Waku This is a Waku instance. Platform query software pgAdmin 4 This is a pgAdmin 4 instance, a web-based administration tool for PostgreSQL. Platform query software Ferron Web Server This is a Ferron web server. Platform query risk React2Shell: Unauthenticated RCE in React Server Components [CVE-2025-55182] This is a critical unauthenticated Remote Code Execution (RCE) flaw, dubbed "React2Shell" caused by insecure deserialization within the Flight protocol used by React Server Components. This risk broadly identifies exposed web services using RSC, but doesn't confirm vulnerability since versions are not available. Users must verify which package versions are running in their environments. ASM query: risks.name: `React2Shell: Unauthenticated RCE in React Server Components [CVE-2025-55182]` risk Vulnerable pgAdmin 4 [CVE-2025-12762] This pgAdmin 4 server is running a version 9.9 or earlier that is vulnerable to CVE-2025-12762, a remote code execution (RCE) vulnerability. When restoring PLAIN-format dump files, an attacker can inject and execute arbitrary commands on the host, potentially leading to full system compromise of the pgAdmin host and downstream database environment. ASM query:risks.name: `Vulnerable pgAdmin 4 [CVE-2025-12762]`
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Nov 24, 2025
Censys Release Notes for November 24, 2025
SummaryAdded the ability to secure your Platform account with multi-factor authentication. Organization admins can enforce MFA for all members of their organization. Use weekly collection digest emails to track changes to your saved Platform queries over time. Two Rapid Response advisories for XWiki and FortiWeb issues. Added fingerprints for Frigate NVR and XWiki and an ASM risk fingerprint for XWiki instances vulnerable to CVE-2025-24893.Platform You can now add another layer of security to your Platform account with multi-factor authentication (MFA) using an authenticator app. Configure your personal MFA settings in Settings > Account Management > Personal Settings > Security. Organization admins can configure MFA enforcement for their organization in Settings > Account Management > Organization Settings > Security. Use collection email notifications to receive weekly messages about updates to your collections. Emails are sent to the email address associated with your user account. Rapid ResponseThe Censys Rapid Response team published information about and queries for the following issues.XWiki Platform Allows Unauthorized RCE Via RondoDox Botnet [CVE-2025-24893] The queries below can help identify exposed XWiki instances, but they cannot determine whether systems are vulnerable. Platform query Legacy Search query ASM query FortiWeb Vulnerability Allows Authenticated OS Command Injection [CVE-2025-58034] The queries below can identify FortiWeb instances but do not filter by version. Platform query Legacy Search query ASM query New fingerprintsAdded the following fingerprints.Type Name Description Query software Frigate NVR Frigate NVR system. Platform query software XWiki This is an XWiki server. Platform query risk Vulnerable XWiki [CVE-2025-24893] XWiki Platform is potentially vulnerable to an unauthenticated remote code execution flaw. If the SolrSearch macro is exposed, an unauthenticated attacker can inject a crafted request into the macro to achieve server-side code execution, which would allow full compromise of the XWiki instance. ASM query: risks.name: `Vulnerable XWiki [CVE-2025-24893]`
Related products:Censys SearchCensys Attack Surface Management (ASM)
Nov 17, 2025
Censys Release Notes for November 17, 2025
SummaryNew AI summary functionality for host assets.Platform Use the new Summarize host functionality on host assets in the UI to quickly generate a concise, human-readable summary of the asset using the Censys Assistant. This feature is available to Starter and Enterprise users.
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
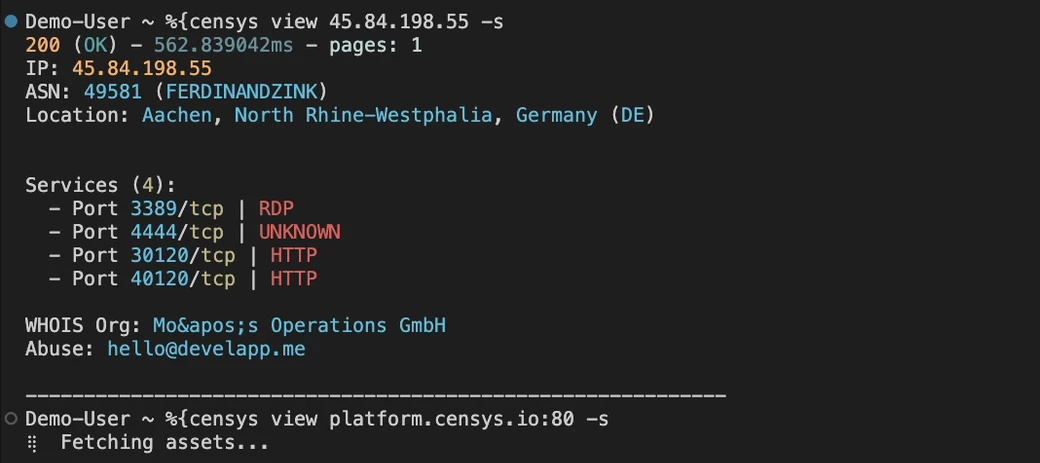
Nov 14, 2025
New Platform Features Available for Free Users
Over the past few weeks, we’ve released several new Censys Platform features for Free users to help them achieve their investigation, research, and hunting goals. You can read all about them in our blog, but the TL;DR is that Free users can now:Use the API to perform asset lookups Create one collection with a max of 100 assets Use the Platform command line tool to execute lookups directly from their terminal View all standard and advanced protocol data in the Platform UI and APIAll of these updates build on our mission to make the Internet safer through greater transparency and accessibility — and ensures that open, high-fidelity Internet data remains available to everyone who needs it.Give the API or CLI a spin today (or view assets in the web UI) to check out all the new features available to Free users.
Related products:Censys Platform
Nov 10, 2025
Censys Release Notes for November 10, 2025
SummaryNew Platform Account Management API endpoints for programmatic organization management and credit monitoring. New fingerprint for Cisco IOS-XE endpoints.Platform Use the Account Management API to programmatically manage your organization and monitor credit consumption. New endpoints are available for the following actions: Get organization details Get organization credit statistics Get organization credit usage Invite user to organization List organization members Remove member from organization Update an organization member's roles Get member credit usage New fingerprintsAdded the following fingerprint.Type Name Description Query operating_system Cisco IOS-XE Endpoints This is a Cisco IOS-XE operating system. Platform query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Nov 3, 2025
Censys Release Notes for November 3, 2025
SummaryCollections are now available to all Free users. One new fingerprint for Tesla Wall Connectors and one new ASM risk fingerprint for exposed Apache ZooKeeper services.Platform Free users can now create and monitor collections in the Platform web console. Collections let you track changes to internet-facing infrastructure to stay proactive about threats and vulnerabilities using a saved Censys query, so you can spend less time searching and more time taking action. Free user collections are limited to 100 assets. New fingerprintsAdded the following fingerprints.Type Name Description Query hardware Wall Connector This is a Tesla Energy Wall Connector. Platform query risk ZooKeeper Service Exposed Apache ZooKeeper is a centralized coordination service used for configuration management, naming, distributed synchronization, and group membership in distributed systems. When ZooKeeper is exposed to the Internet or untrusted networks, attackers may be able to read or modify application configuration and state, enumerate cluster topology, or exploit authentication/ACL misconfigurations to escalate privileges. Exposure can lead to data leakage, service disruption, and full compromise of systems that rely on ZooKeeper for critical coordination. ASM query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Oct 28, 2025
Censys Release Notes for October 27, 2025
SummaryFour risks for exposed Watchguard Firewalls, WDBRPC services, atvremote devices, and KVM devices are now enabled for ASM customers. One new ASM risk fingerprint for BIND 9 resolvers vulnerable to CVE-2025-40778 and one Rapid Response bulletin for this vulnerability.ASMThe following risks have now been enabled by default for all ASM customers.Exposed Watchguard Firewall WDBRPC Service Exposed Exposed atvremote Device Exposed KVMRapid ResponseThe Censys Rapid Response team published information about and queries for the following issue.BIND 9 Resolver Enables Cache Poisoning Via Unsolicited Answers [CVE-2025-40778] The queries below can identify vulnerable BIND 9 resolvers. Platform query Legacy Search query ASM risk query New fingerprintsAdded the following fingerprint.Type Name Description Query risk Vulnerable ISC Bind9 [CVE-2025-40778] This service is running a vulnerable version of ISC Bind9. An attacker may exploit a flaw in DNS response processing that allows cache poisoning via unsolicited answer records, enabling redirection of downstream clients. ASM query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Oct 20, 2025
Censys Release Notes for October 20, 2025
Rapid Response advisory and queries for exposed F5 BIG-IP products affected by recent nation-state breach, threat data now visible for Platform Enterprise customers, and one new fingerprint for Interactsh servers.Platform Some threat data for hosts and web properties is now viewable by all users on Enterprise accounts. The following fields can be seen in the Platform web console and retrieved via API, but may not be searched for or pivoted across unless you also have access to the Threat Hunting module. Data field Description *.threats.id A unique identifier for the threat. *.threats.name Name of the threat, such as Cobalt Strike. *.threats.tactic How the threat behaves and the purpose of the activity, such as COMMAND_AND_CONTROL and PERSISTENCE. *.threats.type The role of the service, such as PHISHING_SERVER and WEBSHELL. Rapid ResponseThe Censys Rapid Response team published information about and queries for the following issue.Nation-State Breach of F5 Networks — Exposure of BIG-IP Source Code & Undisclosed Vulnerabilities The queries below can identify F5 BIG-IP instances, but they cannot determine whether systems are vulnerable. Platform query Legacy Search query ASM query New fingerprintsAdded the following fingerprints.Type Name Description Query software Interactsh Server This is an Interactsh server. Interactsh is an OOB interaction gathering server and client library. Platform query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Oct 13, 2025
Censys Release Notes for October 13, 2025
New cencli command line tool to bring Platform features and data to your terminal, Censys Assistant in the Platform web console for rapid investigations using natural language input, support for integrating the Censys ASM MCP Server with Microsoft Copilot Studio, new fingerprints for Ivanti Endpoint Manager, Oracle Cloud Infrastructure Load Balancer, and Oracle Traffic Director, and one new ASM risk fingerprint for Redis servers vulnerable to CVE-2025-49844.Platform The cencli command line tool enables you to run search queries, look up assets, perform aggregations, and more from your terminal window. cencli can be used by all registered Platform users. Use the Censys Assistant AI tool in the Platform web console to input questions in a natural language and obtain answers based on the assets and data present in the Censys Internet Map. The Censys Assistant is available to all Starter and Enterprise users. ASMIntegrate the Censys ASM MCP Server with Microsoft Copilot Studio to seamlessly incorporate Censys ASM functionality with your AI tools.Rapid ResponseThe Censys Rapid Response team published information about and queries for the following issues.Pre-Auth RCE Chain in Oracle E-Business Suite Software [CVE-2025-61882] The queries below can help identify Oracle E-Business Suite instances, but they cannot determine whether systems are vulnerable. Platform query Legacy Search query ASM query 13 Unpatched Zero-Days in Ivanti Endpoint Manager Enabling RCE The following queries can help identify exposed Ivanti Endpoint Manager / LANDesk instances, but they are not necessarily vulnerable. Platform query Legacy Search query ASM query New fingerprintsAdded the following fingerprints.Type Name Description Query risk Vulnerable Redis Server [CVE-2025-49844] - RediShell This Redis service may be vulnerable to CVE-2025-49844 (RediShell), a critical Use-After-Free vulnerability that allows an authenticated attacker to execute arbitrary code by sending a specially crafted Lua script. The vulnerability affects all Redis versions with Lua scripting support (versions 8.2.1 and below) and has existed in the codebase for approximately 13 years. ASM query: risks.name: `Vulnerable Redis Server [CVE-2025-49844] - RediShell` software Ivanti Endpoint Manager This is Ivanti Endpoint Manager (formerly LANDESK Management Suite), an enterprise endpoint management solution for unified IT operations. Platform query software Oracle Cloud Infrastructure Load Balancer This is an Oracle Cloud Infrastructure (OCI) Load Balancer. An OCI Load Balancer provides automated traffic distribution from one entry point to multiple servers in a set. Platform query software Oracle Traffic Director This is an Oracle Traffic Director. Oracle Traffic Director is a layer-7 software load balancer. Platform query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Oct 6, 2025
Censys Release Notes for October 6, 2025
New Insights experience in ASM to help you understand key data points about your attack surface, unauthenticated access to Platform for easy browsing, new software fingerprints for RustDesk Console, Progress Chef Automate, and ligolo-ng, and a new risk for exposed KVM devices for ASM.ASM Use Insights in ASM to stay on top of key security initiatives like software compliance and vulnerability management. Insights organizes and presents key data points about your attack surface, like the state of your inventory's software and services, in an understandable and easily actionable format. The Insights search bar provides several pre-formatted prompts to help you investigate your inventory and learn how to build useful ASM queries. Insights is available to all ASM users. PlatformAdded the ability to use the Platform without logging in to an account. Use this functionality to look up assets, perform searches, and view shared Platform links. Unauthenticated users can perform a maximum of five actions before they must log in. New fingerprintsAdded the following fingerprints.Type Name Description Query risk Exposed KVM These devices provide keyboard, video, and mouse (KVM) over IP and are used for remote server access. ASM risk query: risks.name: `Exposed KVM` software RustDesk Console RustDesk Console is a self-hosted management interface for RustDesk remote desktop sessions. Platform query software ligolo-ng ligolo-ng is a reverse tunneling and proxy tool for pentesters. Platform query software Progress Chef Automate Progress Chef Automate is a centralized compliance and infrastructure automation platform for Chef configurations across environments. Platform query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Sep 29, 2025
Censys Release Notes for September 29, 2025
New twist function for Platform search queries, matched services in the Platform UI and API, eight new fingerprints, and one Rapid Response bulletin.PlatformUse the new twist function in your Platform queries to find field values that are similar to a specified value. You can use the twist function to find typosquatted domains or domains attempting to impersonate a valid domain by omitting known domains from your query. For example, the following query will find web properties that use names similar to censys.io but will omit results that include censys.io. twist(web.hostname, 'censys.io') and not web.hostname:'censys.io' Use matched services in the UI and API to rapidly find host services that contain data that match your search criteria. Matched services in the UI are shown in the Matched Fields section. Click the service icon to navigate directly to the service card on the host. Matched services in the API are returned in a matched_services object for each host that contains matching data. "matched_services": [ { "protocol": "HTTP", "port": 18083, "transport_protocol": "tcp" } ] The Share link action was moved to the Search Actions menu next to the search bar in the Platform web UI. Use this to generate share links for assets, search query results, and more. Rapid ResponseThe Censys Rapid Response team published information about and queries for the following issue.SNMP RCE in Cisco IOS and IOS XE Software [CVE‑2025‑20352] The queries below can help identify any affected Cisco devices exposing SNMP, but they are not necessarily vulnerable. Platform query Legacy Search query ASM query New fingerprintsAdded the following fingerprints.Type Name Query software NanoKVM Platform query software TinyPilot KVM Platform query software JetKVM Platform query software PiKVM Platform query software BliKVM Platform query software EJOIN SMS Gateway/SimBox Platform query software Ollama AI Model Hosting Platform Platform query software Palo Alto Networks Cortex XSOAR EDL Service Platform query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Sep 22, 2025
Censys Release Notes for September 22, 2025
Platform lookup API endpoints for Free users and three new fingerprints.PlatformAPI Platform lookup API endpoints may now be used by Free users. Lookup endpoints cost 1 credit per asset retrieved, which is the same cost to look up assets in the Platform web UI. Free users can create Personal Access Tokens in the Platform web UI to execute API calls. The lookup endpoints no longer require an organization ID to be executed. If you have access to a Starter or Enterprise organization ID and do not include it in your lookup API call, then the cost is deducted from your Free credit balance. Additionally, the endpoint will only return data that is available to Free users. Free users have access to the following API endpoints: Get a certificate (and get a certificate in PEM format) Retrieve multiple certificates (and retrieve multiple certificates in PEM format) Get a host Retrieve multiple hosts Get a web property Retrieve multiple web properties New fingerprintsAdded the following fingerprints.Type Name Description Query risk GoAnywhere MFT Deserialization Vulnerability [CVE-2025-10035] This service is running a version of GoAnywhere Managed File Transfer software vulnerable to a deserialization vulnerability that could lead to remote code execution. ASM risk query: risks.name: `GoAnywhere MFT Deserialization Vulnerability [CVE-2025-10035]` risk Exposed atvremote Device This device is running atvremote, a tool used to control TV devices over the network. It communicates with services such as AirPlay, Media Remote Protocol (MRP), and Companion API, which are designed for local network use only and should not be exposed to the public internet. If left accessible, attackers could gain unauthorized control of the TV or compromise the device as part of a botnet. ASM risk query: risks.name: `Exposed atvremote Device` software atvremote This is an atvremote server. Platform query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Sep 15, 2025
Censys Release Notes for September 15, 2025
Threat Hunting MCP Server, two new scanners, and two new risk fingerprints.PlatformThreat Hunting ModuleUse the Threat Hunting Model Context Protocol (MCP) Server to give your AI agents access to Censys Threat Hunting APIs, empowering you to find and investigate potential threats at machine speed.New protocol and application scannersAdded scanners for the following services.Protocol/application Query CRESTRON_OVER_IP Platform query MIKROTIK_WINBOX Platform query New fingerprintsAdded the following fingerprints.Type Name Description Query risk Vulnerable SAP NetWeaver AS Java [CVE-2025-42922] SAP NetWeaver AS Java (Deploy Web Service component), versions under J2EE-APPS 7.50, is vulnerable to an insecure file operations issue. The flaw allows an attacker with non-administrative authenticated access to upload arbitrary files through the deployment web service. Once an uploaded file is executed, the attacker may achieve full system compromise. ASM risk query: risks.name: `Vulnerable SAP NetWeaver AS Java [CVE-2025-42922]` risk Vulnerable Sitecore Experience Platform [CVE-2025-53690] Sitecore Experience Manager (XM) and Sitecore Experience Platform (XP) versions through 9.0.2 are affected by a critical deserialization vulnerability tracked as CVE-2025-53690. This vulnerability allows remote attackers to inject arbitrary code through deserialization of untrusted data, potentially leading to remote code execution. ASM risk query: risks.name: `Vulnerable Sitecore Experience Platform [CVE-2025-53690]`
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Sep 8, 2025
Censys Release Notes for September 8, 2025
Google login for Platform and one new software fingerprint.PlatformAdded the ability to log in to the Platform using Google.New fingerprintsAdded the following fingerprint.Type Name Description Query software Cisco Secure Firewall Management Center This is a Cisco Secure Firewall Management Center. Platform query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Sep 2, 2025
Censys Release Notes for September 2, 2025
Cloud CDN Identification for ASM.ASMUse Cloud CDN Identification with ASM Cloud Connectors to understand CDN presence in your attack surface. Cloud CDN Identification finds Azure Front Door CDN and AWS CloudFront software and reports it in the software data provided for host services and web entity instances. You can search for these Cloud CDNs in your inventory by performing a full-text search for the applicable service (such as "CloudFront" or "Front Door") or by searching for the product name in host.services.software.product or web_entity.instances.software.product. All newly set up Azure and AWS Cloud Connectors will ingest cloud CDN information by default. Customers with existing Azure and AWS Cloud Connector configurations need to manually update their Cloud Connectors to begin ingesting this data. To update your Cloud Connector to ingest Cloud CDN data: In the ASM web console, go to Integrations, find your Cloud Connector integration, and click Manage. In the configuration panel, click Edit Configuration, then click Next Step. Click Next Step again. Click Close. Your Cloud Connector is now updated. New fingerprintsAdded the following fingerprint.Type Name Description Query risk Vulnerable Citrix Netscaler Application [CVE-2025-7775, CVE-2025-7776, CVE-2025-8424] This device is vulnerable to multiple critical CVEs: CVE-2025-7775 (memory overflow leading to pre-authentication remote code execution and DoS), CVE-2025-7776 (memory overflow causing unpredictable behavior and DoS), and CVE-2025-8424 (improper access control on management interface). These vulnerabilities have been actively exploited in the wild since June 2025. ASM query: risks.name: `Vulnerable Citrix Netscaler Application [CVE-2025-7775, CVE-2025-7776, CVE-2025-8424]`
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Aug 25, 2025
Censys Release Notes for August 25, 2025
Historical hosts for certificate API, Investigation Manager enhancements, and three new fingerprints.PlatformThreat HuntingUse the get host history for a certificate API to retrieve the historical observations of hosts associated with a certificate. This is useful for threat hunting, detection engineering, and timeline generation.Investigation Manager Added the ability to create investigations directly from host, certificate, web property, and collection pages. Added an asset node details card for hosts that includes geographic location, labels, reverse and forward DNS, service ports and protocols, and more contextual data. This card appears when you click on host nodes in the investigation manager UI. Added a minimap to the bottom right corner of the investigation UI to make it easier to navigate your investigations.Rapid ResponseThe Censys Rapid Response team published information about and queries for the following issue.Plex Warns Users to Patch Security Vulnerability in Plex Media Server Use the following queries to find Plex Media Server login portals. Not all of these are necessarily vulnerable. Platform query Legacy Search query ASM query New fingerprintsAdded the following fingerprints.Type Name Description Query risk WDBRPC Service Exposed This service is running WDBRPC (VxWorks WDB Remote Proceudre Call), a debugging protocol used by VxWorks real-time operating systems. WDB enables remote debugging, memory access, and system control of embedded devices. Exposure allows attackers to read/write system memory, execute arbitrary code, access sensitive data, or completely compromise the embedded system. ASM query: risks.name: `WDBRPC Service Exposed` risk Vulnerable N-able N-central [CVE-2025-8875 & CVE-2025-8876] This is a service running a version of N-able N-central that is vulnerable to CVE-2025-8875 and CVE-2025-8876. ASM query: risks.name: `Vulnerable N-able N-central [CVE-2025-8875 & CVE-2025-8876]` software N-able N-central This is an N-able N-central Remote Monitoring & Management solution. Platform query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Aug 18, 2025
Censys Release Notes for August 18, 2025
New MCP server for ASM and new Platform scan and query conversion APIs.ASMUse the ASM Model Context Protocol (MCP) Server to give your AI agents and workflows secure, governed, and direct access to your ASM inventory, empowering you to explore and understand your attack surface at machine speed.PlatformAPIAdded new API endpoints for Live Rescan, Live Discovery, and retrieving scan status. Added a new API endpoint for converting Legacy Search queries into Platform queries.Bug fixesFixed an issue that caused some large number values, such as Cobalt Strike watermarks, to display in scientific notation.New protocols and application scannersAdded support for the following protocols and applications.Protocol/application Query ASTERISK_MANAGER_INTERFACE Platform query ODETTE_FTP Platform query OPENVPN_MGMT Platform query New fingerprintsAdded the following fingerprint.Type Name Description Query software/hardware Wavlink Router This is a Wavlink Router. Platform query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Aug 11, 2025
Censys Release Notes for August 11, 2025
Download search results for Core and Enterprise users, new API endpoints for retrieving certificates in PEM format, five new fingerprints, and one Rapid Response bulletin.Platform Core and Enterprise users can now download search results in CSV format in the Platform UI. Each page of results must be downloaded separately. Each CSV file can contain a maximum of 100 results. APIAdded two new API endpoints to retrieve a single certificate or multiple certificates in PEM format.Rapid ResponseThe Censys Rapid Response team published information about and queries for the following issue.High-Severity Flaw Affecting Microsoft Exchange Hybrid Deployments [CVE-2025-53786] Use the following queries to find Exchange servers that may or may not have an OWA portal present. Not all of these are necessarily vulnerable. Read the blog for more information about finding OWA portals and hosts with Exchange servers and OWA portals on the same device. Platform query Legacy Search query ASM query ASM risk query New fingerprintsAdded the following fingerprints.Type Name Description Query risk Vulnerable Exchange Server [CVE-2025-53786] The Microsoft Exchange application is running a version that is potentially vulnerable to CVE-2025-53786, which allows privilege escalation on on-premises Exchange Servers configured as hybrid deployments. ASM risk query: risks.name: `Vulnerable Exchange Server [CVE-2025-53786]` risk Vulnerable Papercut Print Server CVE-2023-2533 This Papercut MF/NG Print Server is vulnerable to CVE-2023-2533, a CSRF vulnerability that could potentially allow an attacker to alter security settings or execute arbitrary code. This can be only be exploited if the target is an admin with a current login session, and often times requires the user to click a specially crafted malicious link. Versions \< 20.1.8, 21.0.0 - 21.2.11, and 22.0.0 - 22.1.0 are affected. ASM risk query: risks.name: `Vulnerable Papercut Print Server CVE-2023-2533` software Oracle E-Business Suite Oracle E-Business Suite is an integrated set of business applications that helps enterprises manage core functions like finance, supply chain, human resources, and customer relationship management. Platform query software Papercut NG Print Server Papercut NG is a print management system. Platform query software Papercut MF Print Server Papercut MF is a print management system. Platform query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Aug 4, 2025
Censys Release Notes for August 4, 2025
Query Assistant improvements in the Platform and seventeen risks enabled for ASM.PlatformYou no longer need to click the generate button to convert natural language input into a Censys Query Language query using the Query Assistant. Instead, the query assistant now automatically converts natural language after you enter it.ASMThe following risks are now enabled for all ASM customers.Risk name Description Severity ATG (Automatic Tank Gauging) Service Exposed This service is running Automatic Tank Gauging (ATG) protocol used for monitoring fuel tanks and fluid levels in critical infrastructure. ATG systems control fuel distribution, inventory management, and leak detection systems. Exposure allows attackers to manipulate fuel readings, cause environmental damage, or disrupt operations. Critical OPC UA Service Exposed This service is running OPC Unified Architecture (OPC UA), a critical industrial communication protocol used for data exchange between industrial equipment, SCADA systems, and manufacturing execution systems. Exposed OPC UA servers allow attackers to read sensitive operational data, modify control parameters, or disrupt industrial processes. Critical GE SRTP Service Exposed This service is running GE SRTP (General Electric Service Request Transport Protocol), used for communication with GE industrial control systems, PLCs, and automation equipment. GE SRTP enables configuration, monitoring, and control of critical infrastructure equipment. Exposure allows attackers to access control systems, modify operational parameters, or cause equipment failures. Critical PCWORX Service Exposed This service is running PCWORX protocol, used by Phoenix Contact PLCs and industrial automation systems. PCWORX enables programming, configuration, and real-time communication with industrial controllers in manufacturing, building automation, and process control applications. Exposure allows attackers to read/write PLC programs, modify control logic, or disrupt automated processes. Critical IEC 60870-5-104 Service Exposed This service is running IEC 60870-5-104, a critical power system communication protocol used for telecontrol and SCADA in electrical power systems. This protocol controls power generation, transmission, and distribution infrastructure. Exposure allows attackers to manipulate power grid operations, cause blackouts, or damage electrical equipment. Critical MMS (Manufacturing Message Specification) Service Exposed This service is running Manufacturing Message Specification (MMS), an ISO standard for real-time communication in industrial automation systems. MMS enables communication between SCADA systems, DCS controllers, and manufacturing equipment. Exposure allows attackers to read critical process data, modify control parameters, or disrupt manufacturing operations. High HART Service Exposed This service is running HART (Highway Addressable Remote Transducer) protocol, used for communication with smart field devices in process automation. HART enables digital communication with sensors, transmitters, and actuators in chemical plants, refineries, and other industrial facilities. Exposure allows attackers to read process measurements, modify device configurations, or disrupt critical control loops. High UBIQUITI Service Exposed This service is designed for Ubiquiti device management and configuration. Ubiquiti devices often have default credentials and known vulnerabilities, making them attractive targets for attackers seeking to gain network access or use devices in botnet attacks. High NETIS Service Exposed This service is running the NETIS router configuration protocol. NETIS routers have a well-known backdoor vulnerability (CVE-2014-2321) that allows unauthenticated remote access via UDP port 53413. This backdoor has been widely exploited by malware and botnets for gaining network access and launching attacks. Critical SSDP Service Exposed This service is running the Simple Service Discovery Protocol (SSDP), which is part of the UPnP protocol suite. SSDP is a major vector for DDoS amplification attacks with amplification factors up to 30x. It also exposes detailed device information that can be used for network reconnaissance and targeted attacks. High WS-Discovery Service Exposed This service is running Microsoft's Web Services Dynamic Discovery (WS-Discovery) protocol used for device and service discovery on networks. When exposed to the Internet, it can be abused for DDoS amplification attacks and allows attackers to gather detailed information about internal network devices and services. Medium TP-Link Kasa Service Exposed This service is running TP-Link Kasa smart home device management protocol. Exposed Kasa devices allow unauthorized users to control smart plugs, lights, cameras, and other IoT devices, potentially enabling privacy invasion, device manipulation, or using devices as entry points for further network attacks. Medium Chromecast Service Exposed This service is designed for Google Chromecast streaming and control functionality. Exposed Chromecast devices can allow unauthorized users to hijack media streaming, play unwanted content, or use the device as an entry point for network reconnaissance and attacks. Medium Yahoo Smart TV Service Exposed This service is designed for Yahoo Smart TV functionality and remote control capabilities. Exposed Smart TV services can be targets for unauthorized access, privacy invasion through camera/microphone access, or incorporation into IoT botnets for DDoS attacks. Medium IOTA Service Exposed This service is part of the IOTA distributed ledger technology ecosystem. Exposed IOTA nodes can be targets for cryptocurrency-related attacks, DDoS amplification, or exploitation of node software vulnerabilities. Medium DCERPC Service Exposed The Distributed Computing Environment / Remote Procedure Call (DCERPC) protocol is used by many Windows services for remote management, authentication, and service control. It operates by default over port 135/TCP. Exposure of DCERPC services to the internet can allow attackers to enumerate available services, exploit unpatched vulnerabilities, and potentially execute remote code. DCERPC should never be exposed directly to the internet without strict access controls. High WINRM Service Exposed Windows Remote Management (WinRM) is a Microsoft protocol used for remotely managing Windows systems via PowerShell and other tools. While powerful for automation and administration, exposing WinRM to the internet is dangerous because it can allow attackers to execute remote commands, especially if using weak or default credentials. It supports basic and NTLM authentication, which can be intercepted or brute-forced, particularly over unencrypted HTTP (port 5985). Without proper safeguards like VPN access, strong auth, and firewalls, an exposed WinRM service is a high-risk entry point for attackers. High
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Jul 31, 2025
Censys Release Notes for July 31, 2025
Open directory data enhancements and suspicious directory threat, graphical investigation explorer, CensEye enhancements, and more improvements in the Platform; Chrome browser extension, and registrant email domain pivoting in ASM.PlatformThreat HuntingBuild node-based pivot trees to discover, visualize, and understand connections between web assets in the Censys datasets using the Investigation Manager in the Platform web UI. Use the Suspicious Directory threat to find and track web assets with open directories that contain security tools, penetration testing utilities, webshells, or other potentially malicious files. Use this threat information to find hosts and web services with suspicious files before they are leveraged in attacks. Leverage the open directory visual explorer and open directory parsed fields to quickly understand directory information at a glance, including file names, sizes, last modified dates, and directory structure. Made several changes to the default CensEye pivot fields for hosts, web properties, and certificates, including: Added TLS fingerprinting fields (JA4S, JA3S, JA4X, JARM) for better network analysis Added SSH, Cobalt Strike, and protocol-specific pivots for threat detection Added HTTP metadata fields (headers, favicons, body hashes) for web analysis Switched favicon hashes from MD5 to SHA256 for improved security Added support for specialized protocols including SCADA, Kubernetes, and SNMP Chrome browser extensionPerform IP lookups and full-text searches from within a browser window using the Censys Chrome browser extension.APIAdded the count_by_level parameter to the aggregate endpoint to allow you to specify which document level's count is returned per term bucket, primarily for nested fields. This is the same functionality available in the Count By dropdown in the Report Builder UI.ASMAdded registrant email domain pivoting to the ASM attribution process during seed discovery. If ASM finds the email address registrant@censys.com associated with a domain that belongs to you, it will pivot to find other assets registered to any censys.com email address. If you accept an email domain as a seed, you will see many new registrant emails appear in the seed discovery list. If you have continuous seed discovery enabled, this update may result in more frequent seed discovery emails for newly found email addresses. Rapid ResponseThe Censys Rapid Response team published information about and queries for the following issue.Critical CrushFTP Vulnerability Added to CISA KEV [CVE-2025-54309] Use the following queries to find CrushFTP servers. Not all of these are necessarily vulnerable. Platform query Legacy Search query ASM query ASM risk query New fingerprintsAdded the following fingerprints.Type Name Description Query risk Vulnerable CrushFTP [CVE-2025-54309] CrushFTP 11 before 11.3.4_23 (update \< 756), when the DMZ proxy feature is not used, is vulnerable to CVE-2025-54309 due to mishandled AS2 validation, allowing remote attackers to obtain admin access via HTTPS. ASM risk query: risks.name: `Vulnerable CrushFTP [CVE-2025-54309]` software Cisco ISE Cisco Identity Services Engine (ISE) is a network access control and policy enforcement system that provides secure access via identity-based policies. Platform query
Related products:Censys SearchCensys Attack Surface Management (ASM)Censys Platform
Filter by product
- All products
- Censys Attack Surface Management (ASM)
- Censys Search
- Censys Platform
Sign up
Already have an account? Login
You need a Censys account in order to create a Censys Community account. When you click the button below, you will be redirected to login using your existing Censys credentials. If you do not already have a Censys Community account, you will be prompted to create one after logging into your Censys account.
Log in or register with Censys credentials
Log in to the Censys Community
You need a Censys account in order to create a Censys Community account. When you click the button below, you will be redirected to login using your existing Censys credentials. If you do not already have a Censys Community account, you will be prompted to create one after logging into your Censys account.
Log in or register with Censys credentials
Enter your E-mail address. We'll send you an e-mail with instructions to reset your password.
Scanning file for viruses.
Sorry, we're still checking this file's contents to make sure it's safe to download. Please try again in a few minutes.
OKThis file cannot be downloaded
Sorry, our virus scanner detected that this file isn't safe to download.
OK