CVE risk rescan and scan data links in ASM, three new software fingerprints, and one new Rapid Response bulletin.
ASM
-
Use the ability to rescan CVE risks on host risk cards in the ASM web console to verify that a CVE risk has been closed after completing your or remediation workflows. Use the View Scan Data button to see the scan data for the service.
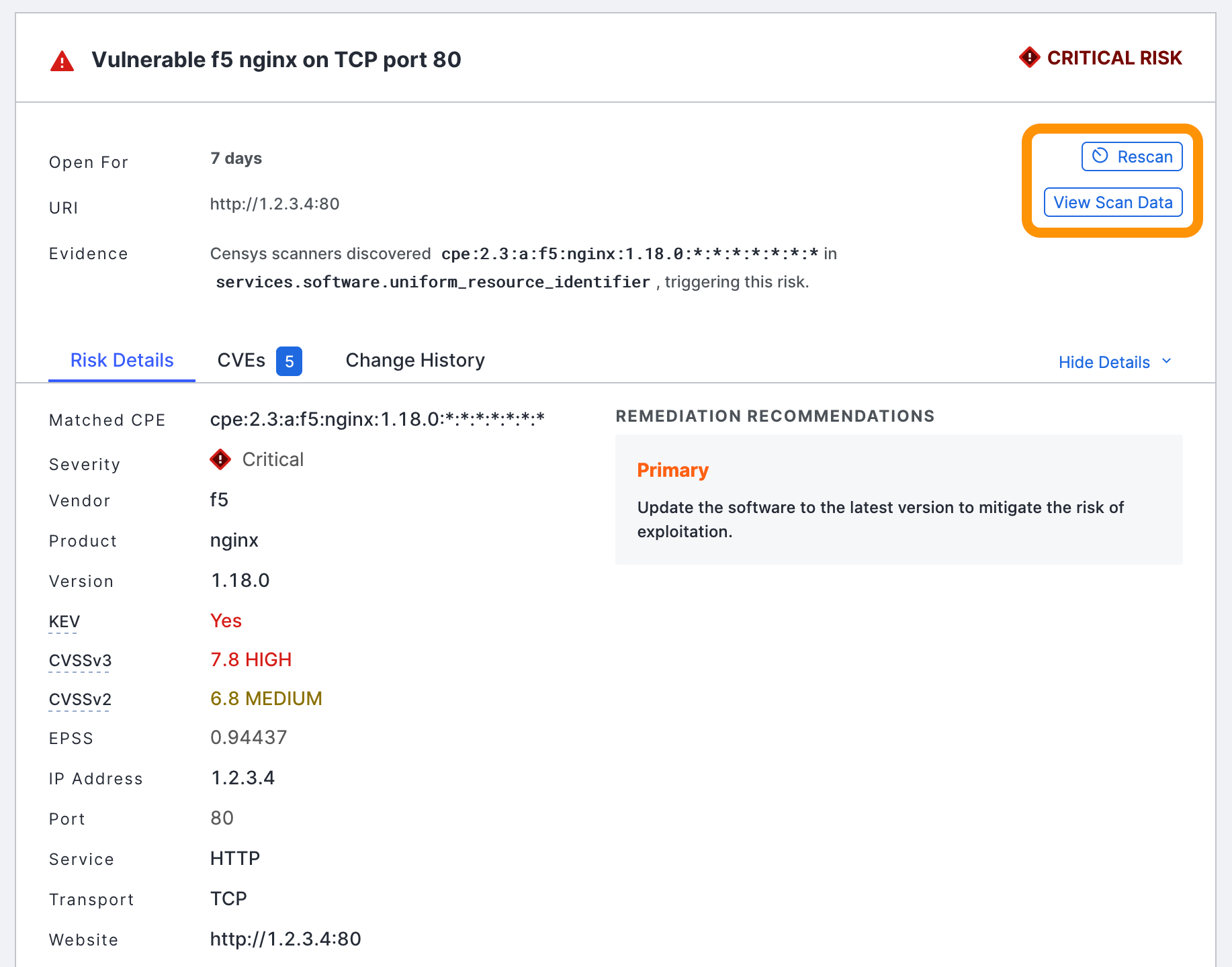
-
Added the ability to copy data field names from table header rows in the ASM web console to quickly search your inventory for relevant assets.
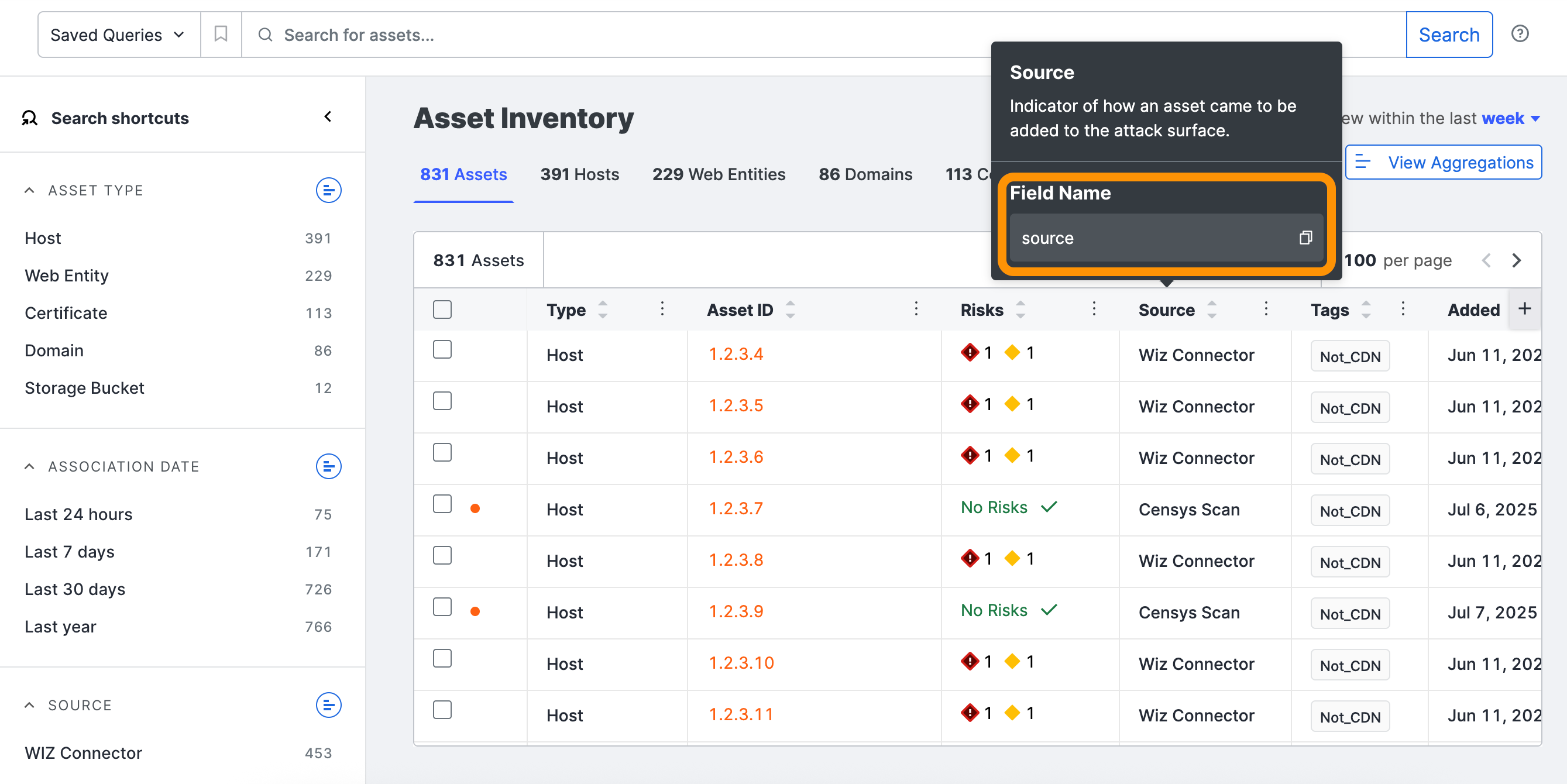
New fingerprints
Added the following fingerprints.
| Type | Name | Description | Query |
|---|---|---|---|
| software | MCP Inspector | MCP Inspector is a developer tool that enables inspection and debugging of Model Context Protocol workflows. | Platform query |
| software | BentoML | BentoML is an open-source platform designed to help developers package and deploy machine learning models. | Platform query |
| software | AMI MegaRAC SP-X Firmware | This is a device running AMI MegaRAC SP-X firmware, a proprietary Linux-based platform for Baseboard Management Controllers (BMCs). MegaRAC SP-X provides out-of-band management functionality via interfaces like Redfish, IPMI, and a web GUI, and is commonly deployed in enterprise servers and datacenter hardware. | Platform query |
Rapid Response
The Censys Rapid Response team published information about and queries for the following issue.
- Multiple Vulnerabilities in NetScaler Gateway & ADC [CVE-2025-5777 & CVE-2025-6543 & CVE-2025-5439]
- Use the following queries to identify exposed MegaRAC SPx firmware. Not all of these are necessarily vulnerable, as specific version information may not be available.

