“at the end of the day, it’s not actually computer-to-computer, right?” he said. “The technology is a vector for human beings. Behind the connection is a person." - Nate Fick, US State’s ambassador for cyber.
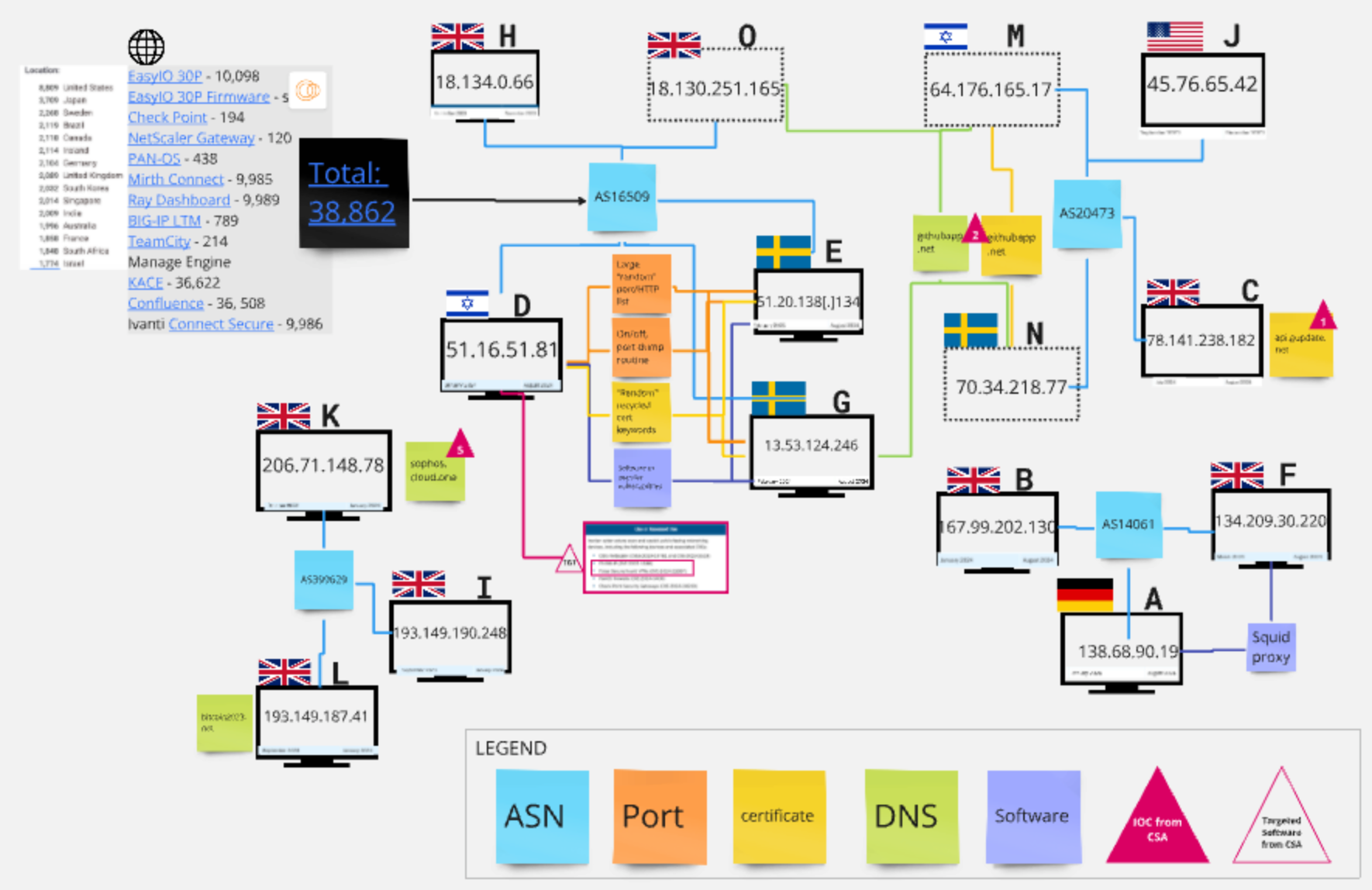
Using this mentality, and the fact that humans have patterns, I dug into IOCs from the Joint Cybersecurity Advisory on Iranian threat actor group “Fox Kitten” to uncover hosts that shared either identical IOCs or similar patterns (ports, software, certificates, DNS, etc) and therefore, are likely part of their infrastructure that wasn’t mentioned in the report. Check out the analysis here.
Specifically, a search for domain IOCs from the Advisory yielded the following IPs with those IOCs in their DNS and certificate records. These IPs were not listed in the Advisory yet share Autonomous Systems/networks with host IOCs that are listed in the Advisory, further linking them to the group.
- “Host M” - 64.176.165[.]17
- “Host N” - 70.34.218[.]77
- “Host O” - 18.130.251[.]165
What does this mean for threat hunters and defenders? By using Censys’ history and pivoting features, one can see if threat IOCs have friends, which means being protected against potential future threats that others will miss.

